Microsoft recently published a critical security advisory on 2 vulnerabilities, CVE-2025-53770 and CVE-2025-53771, affecting on-premises Sharepoint servers. Though Microsoft has now made security updates available for these vulnerabilities (referred to as ToolShell exploit), this was labeled as a critical 9.8 CVSS zero day vulnerability. If your organization has Microsoft SharePoint Server 2019 or Microsoft SharePoint Server 2016 that’s exposed to the internet, make sure these have the latest security updates from Microsoft.
But, security for your organization cannot be this reactive. Several large organizations, US government agencies and critical infrastructure providers were affected by this vulnerability, despite having strong perimeter defenses like firewalls, IDS and IPS systems.
What Really Happened?
The ToolShell attack was a strategic execution that proved that traditional perimeter security is no longer effective against the modern adversary. The vulnerability was possible because the SharePoint server was exposed, and easily accessible from the internet. The adversary exploited the CVE-2025-53771 vulnerability, bypassing authentication by sending a specially crafted request that was trusted by the exposed SharePoint servers. Of course, this was seen as a legitimate request and the perimeter firewall let it pass, opening the front doors to the adversary.
Once the adversary got the foothold into the server, they exploited a critical remote code execution flaw (CVE-2025-53770) to run commands and made the server execute the malicious payload that was disguised as normal application data. Finally, the adversaries used remote access to grab the server’s cryptographic machineKey; the ValidationKey and DecryptionKey, eventually giving them persistent, authenticated access to the machines.
Impacted on-prem SharePoint versions:
- SharePoint Server Subscription Edition
- SharePoint Server 2019
- SharePoint Server 2016
Microsoft recommends patching these servers and also highlights that their cloud-hosted Microsoft 365 SharePoints are unaffected by this breach.
Defending Against These Vulnerabilities: Make Your Sharepoint Servers Invisible to Adversaries
Instead of the traditional castle-and-moat strategy for protecting your SharePoint servers, you must shift to a strategy that makes the servers invisible to adversaries. Moving from traditional perimeter-based defenses to secure overlay networks built on the foundational principles of Zero Trust should be your go to strategy that will empower you to enable proactive security.
Secure On-Premises Sharepoint Servers With Netbird Networks
NetBird, built on the industry-proven, high-performance WireGuard® protocol creates radically simple and secure overlay networks. Simply install the super-lightweight NetBird agent on your users’ devices - be it on Windows/Mac laptops, workstations or mobile devices (iOS and Android) or even Docker containers.
Further, in your environment, if you cannot or do not wish to install an agent—such as SharePoint servers, managed database services (e.g., AWS RDS), printers, legacy servers, or sensitive IoT devices, NetBird Networks feature provides a powerful, secure and super-simple remote access. With NetBird Networks simply deploy one or more NetBird agents as ' routing peers ' inside your private network segments (like an AWS VPC or an on-premise LAN). NetBird ensures robust connectivity with built in high availability . You get the flexibility to install multiple routing peers to avoid a single point of failure.
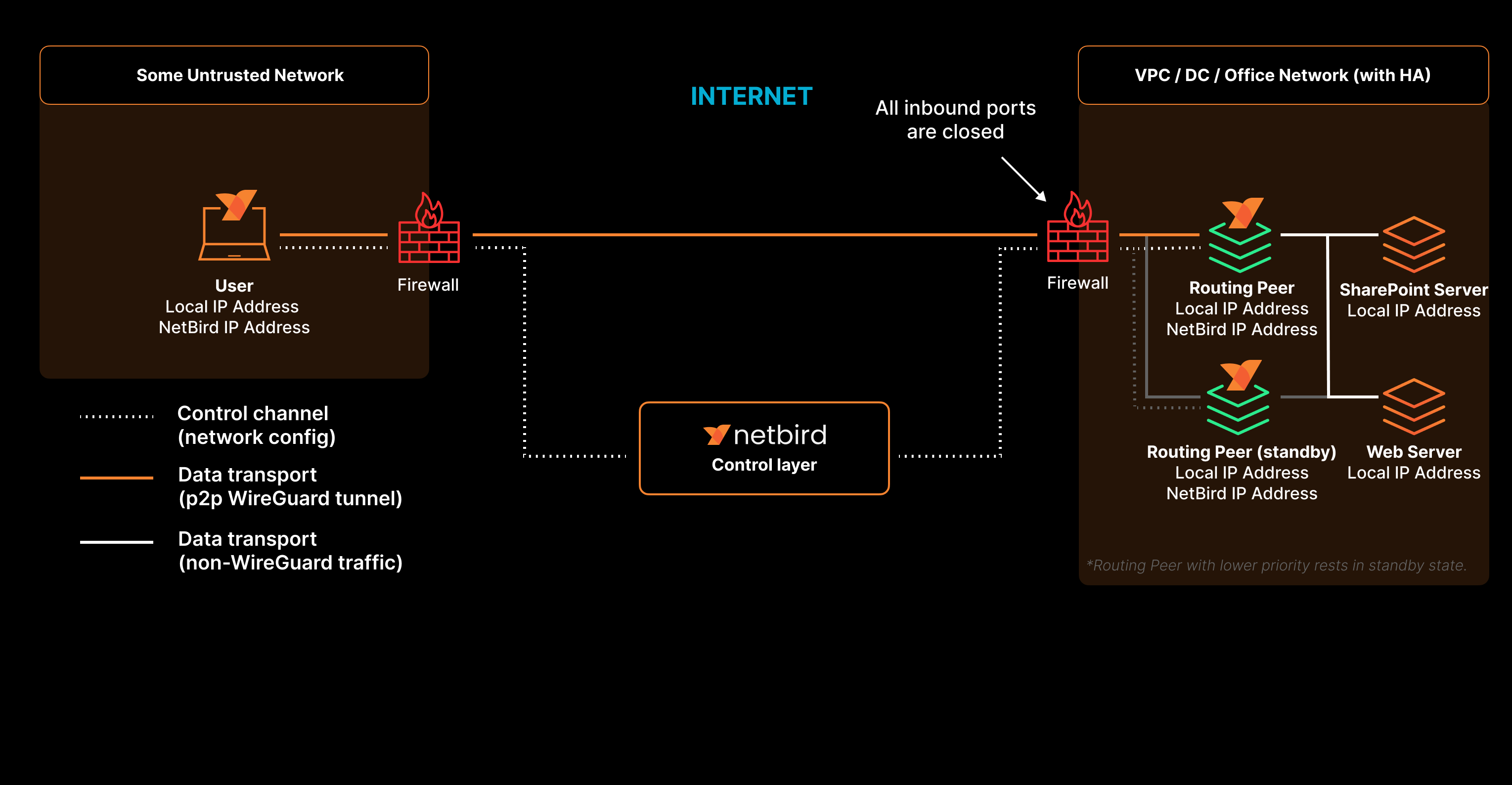
NetBird establishes encrypted tunnels between your user devices and routing peers without a need for open ports, effectively ‘cloaking’ your SharePoint servers from the public internet. This means that your SharePoint servers will no longer have their public IPs exposed, to be scanned, probed or exploited by adversaries. Your SharePoint server is accessible only to other authenticated and authorized peers and users within the private NetBird network. With this simple architectural change, you eliminate the external threat surface that adversaries rely on for initial reconnaissance and exploitation. The adversary simply cannot attack what they cannot see.
Remove Entry Points Into the Network by Eliminating Open Firewall Ports
NetBird Networks gives you the confidence to close inbound ports on your firewalls. This unique feature of NetBird doesn't require open ports in the firewall, enabling you to establish connections even when all inbound ports are closed. When your users access SharePoint, their devices establish a direct, encrypted tunnel to the server, completely eliminating the risk of ToolShell attacks. Since NetBird is built from the ground up on the core principles of Zero Trust, you will now move from the ‘allow by default’ on your firewalls to ‘deny by default’, only allowing access tied to identities and the principle of least privileges.
| Methodology | Perimeter Security | NetBird Zero Trust |
|---|---|---|
| Access Posture | Allow by default (loved by adversaries!) | Deny by default |
| Trust Posture | IP addresses | Identity and context (user + device). Secure by default |
| Exposure | Visible to adversaries (exposed critical apps/servers) | Cloaked (invisible to the public internet) |
| Access Control | Port-level | Granular: Restrict access to specific servers/services/apps for specific users, user groups, based on identity, context and device posture |
Conclusion
The ToolShell exploit on on-premises SharePoint servers is a clear message that exposes the flaws of traditional perimeter-based infrastructure. We strongly advise you to patch your SharePoint servers immediately, following Microsoft’s security guidance. No organization can afford to continue this highly reactive and disruptive security path. By adopting NetBird’s Zero Trust overlay networks, you can decisively shift to a proactive security posture, making your critical infrastructure invisible to attackers.
“NetBird has fundamentally transformed our network management operations, eliminating outages, simplifying operations, and enabling secure, scalable connectivity through code. What used to be a fragile, error-prone setup is now a robust, policy-driven system that fits the way we structure and secure our infrastructure.” - Sport Alliance
