Tailscale's proprietary coordination server creates a vendor dependency that regulated industries, air-gapped environments, and sovereignty-focused organizations cannot accept. Teams managing sensitive workloads need alternatives where every component, from data plane to coordination infrastructure, can be audited and self-hosted.
This roundup evaluates five open source networking platforms that eliminate vendor lock-in. We compare self-hosting capabilities, management tooling, and operational requirements across solutions ranging from commercially backed platforms with enterprise features to pure community tools demanding technical expertise.
1. NetBird
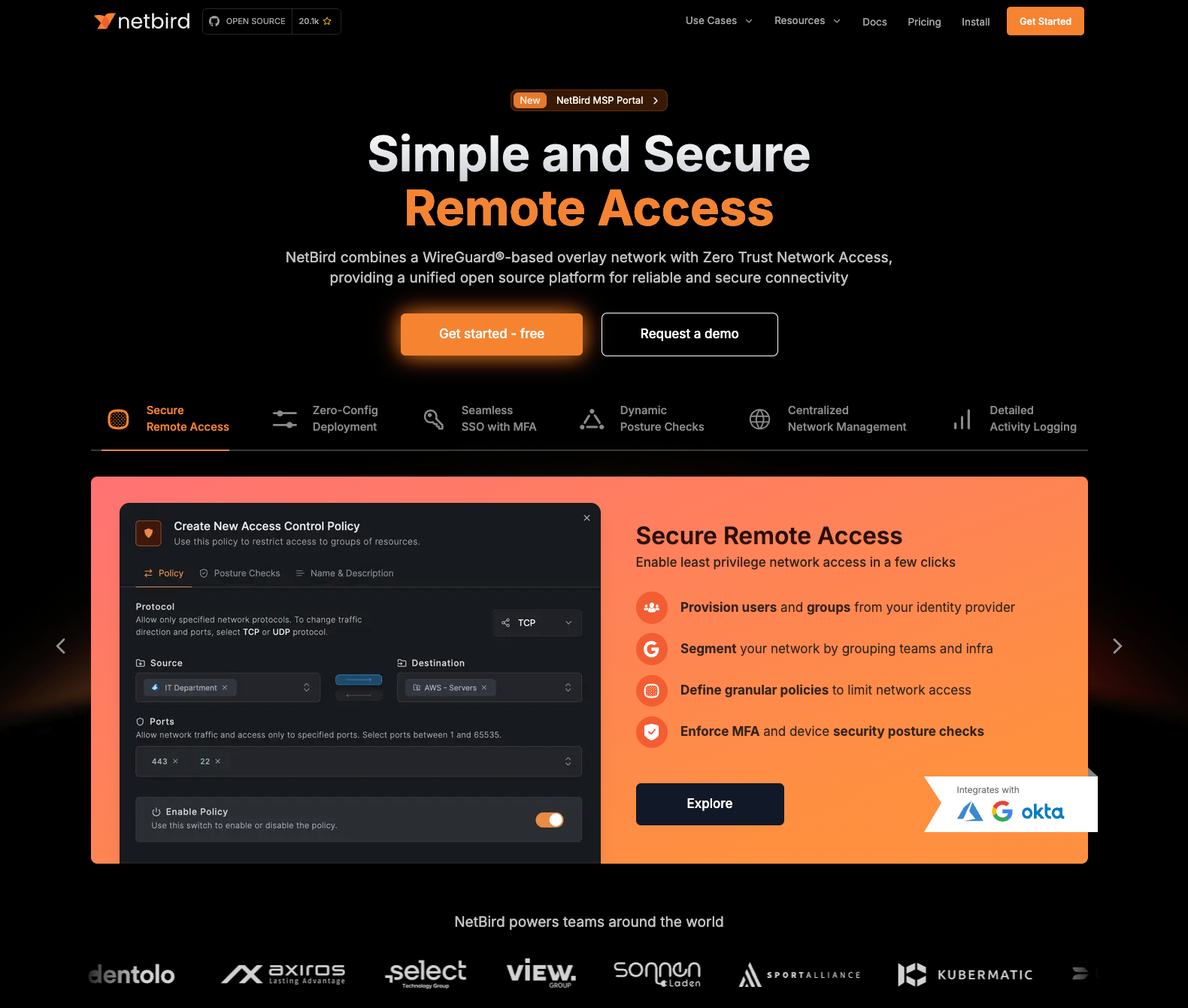
NetBird is an open source Zero Trust networking platform built on the WireGuard protocol, maintained by a Berlin-based team. The platform is primarily licensed under AGPLv3, enabling organizations to deploy and audit the complete stack. Unlike Tailscale, NetBird's entire coordination infrastructure (management service, signal server, and relay routing) can be self-hosted and operated independently.
Why choose NetBird over Tailscale?
NetBird eliminates Tailscale's core architectural dependency: the proprietary coordination server. Every component can be self-hosted, inspected, and operated on infrastructure you control, critical for organizations in regulated industries (GDPR, HIPAA, SOC 2) where auditing third-party infrastructure presents compliance challenges. While Tailscale allows self-hosting relay servers (DERP), the coordination plane itself remains cloud-locked.
NetBird's rapid feature development demonstrates platform maturity beyond basic mesh networking:
- Control Center: Interactive topology visualization showing real-time peer relationships, group memberships, and access policy flows, enabling administrators to audit "who can access what" at a glance. Tailscale lacks comparable visual topology mapping.
- Self-Hosted Identity-Aware SSH: Deploy SSH certificate authority logic entirely on your infrastructure while authenticating sessions through your IdP using OIDC tokens. While Tailscale SSH offers similar functionality, it requires their proprietary coordination plane. NetBird enables this capability in both cloud-based and on-premise environments where the coordination server itself runs on infrastructure you control.
- Complete Infrastructure Control: Self-host management services, signal coordination, and relay routing without dependency on external providers. NetBird allows ownership of the entire stack; a critical distinction for compliance frameworks requiring auditable infrastructure.
Although NetBird is rapidly closing the feature gap, its ecosystem still lacks the depth of third-party integrations found in Tailscale. Furthermore, self-hosting NetBird requires operational expertise to manage the coordination infrastructure that Tailscale handles automatically.
Is NetBird free for commercial use?
Yes, NetBird's free tier supports up to 5 users and 100 machines with full peer-to-peer encryption, SSO authentication, access controls, private DNS, and subnet routing; suitable for proof-of-concept deployments. The Team plan ($5 per user monthly) adds unlimited users, audit logging, and automated user/group provisioning via SCIM from your IdP. The Business plan ($12 per user monthly) includes posture checks, traffic event logging, and EDR integrations for Zero Trust enforcement.
Self-hosted deployments access core connectivity features and SSO authentication without licensing fees, though cloud-exclusive management capabilities (automated SCIM provisioning, SIEM streaming, peer approval workflows) require paid cloud plans.
Quick Verdict: Best for organizations requiring production-ready Zero Trust networking with full infrastructure control and audit transparency. Ideal for regulated industries where data sovereignty requirements or compliance frameworks mandate self-hosted coordination infrastructure.
2. Headscale
Headscale is an open source, self-hosted implementation of the Tailscale control server, released under the BSD 3-Clause license. Rather than building an independent networking platform, Headscale replicates Tailscale's coordination protocol, allowing organizations to run official Tailscale clients against infrastructure they operate, delivering Tailscale's client experience without dependency on Tailscale's commercial SaaS backend.
Why choose Headscale over Tailscale?
Headscale eliminates the commercial control plane entirely while preserving compatibility with Tailscale's production-tested clients across all platforms. Organizations gain complete sovereignty over coordination infrastructure: user authentication, node registration, and network policy, without maintaining a fork of the client software itself. This proves valuable for teams that trust Tailscale's client implementation but cannot route coordination traffic through external SaaS infrastructure.
This approach delivers immediate access to Tailscale's mature client ecosystem, including mobile applications and platform integrations (via 'Custom Control Server' configuration settings), while avoiding the engineering overhead of maintaining cross-platform client software.
Headscale's key features for self-hosted Tailscale coordination include:
- Tailscale Client Compatibility: Works seamlessly with official Tailscale clients on Linux, Windows, macOS, iOS, and Android; no custom client installation required. Supports Tailscale-compatible pre-authentication keys for non-interactive node registration, facilitating automated provisioning in CI/CD pipelines.
- SQLite-Based Architecture: Uses a single SQLite database for state management, simplifying backup and migration workflows compared to distributed database requirements.
- Command-Line Administration: Manages users, nodes, and authentication keys entirely through CLI commands, enabling infrastructure-as-code workflows and automation for administrators who prefer scriptable tools over graphical interfaces.
Headscale operates exclusively through command-line tools without a built-in web interface. While third-party management UIs like Headplane exist, they introduce additional components to deploy and maintain. The platform also implements a single tailnet model per instance, limiting applicability to multi-tenant scenarios that require isolated network boundaries for different teams or customers.
Is Headscale free for commercial use?
Yes, Headscale is released under the BSD 3-Clause license with no usage restrictions or commercial limitations. Organizations can deploy unlimited instances and connect unlimited nodes without licensing costs, though the single-tailnet architecture inherently limits its applicability to large multi-tenant environments.
Quick Verdict: Best for self-hosters and technical teams comfortable with command-line workflows who want to run Tailscale clients against private infrastructure. Ideal for homelab enthusiasts, small open-source projects, and administrators who prefer scriptable tools over graphical interfaces. Not suitable for organizations requiring web-based management dashboards or multi-tenant network isolation without deploying multiple separate instances.
3. Netmaker
Netmaker is an open source platform for building WireGuard-based software-defined networks, with core components licensed under Apache 2.0 and the management UI under SSPL. Unlike platforms requiring proprietary agents, Netmaker supports both a headless agent (netclient) and standard WireGuard configuration files, enabling organizations to integrate diverse device types like Linux servers, IoT devices, and network routers into centrally managed mesh topologies.
Why choose Netmaker over Tailscale?
Netmaker's architecture enables simultaneous connection to multiple isolated networks from a single client using separate virtual interfaces, a capability Tailscale's flat network model cannot natively support. Where Tailscale requires switching between separate tailnets or using ACLs within one network for segmentation, Netmaker provides network-level isolation as a first-class primitive. This proves valuable for organizations managing dozens of networks, enterprises requiring strict production/staging separation, or IoT deployments partitioning device traffic by security zone.
Key capabilities distinguishing Netmaker's approach:
- Multi-Network Segmentation: Creates multiple isolated virtual networks within a single deployment, enabling tenant separation or use-case-specific topologies without deploying separate control planes. A single client can participate in multiple networks simultaneously via distinct virtual interfaces.
- Native WireGuard Configuration Support: Generates standard WireGuard files for router and IoT integration, eliminating agent installation requirements on network infrastructure. This enables universal compatibility with WireGuard-capable devices, where Tailscale's proprietary protocol requires their agent on all endpoints.
- Flexible Client Models: Supports headless mesh agents for full automation, manual WireGuard configs for infrastructure devices, and remote access clients for end-user connectivity, addressing diverse deployment scenarios within one platform.
Keep in mind that Netmaker's multi-network architecture introduces operational complexity unsuited to simple single-network deployments where Tailscale's streamlined model suffices. The platform's smaller ecosystem also means fewer integrations and community resources compared to established alternatives.
Is Netmaker free for commercial use?
Yes, Netmaker's self-hosted Community edition is free with unlimited devices, networks, and users under Apache 2.0 and SSPL licensing. This edition provides core mesh networking capabilities, though advanced features like metrics, remote access clients, automated failover, and comprehensive user management require paid tiers.
The Team plan targets organizations replacing legacy VPNs, priced at $2.75 per active connection monthly (with a $10 platform fee). For 100 connections and one network, this totals approximately $285 monthly. The Business plan adds IdP provisioning, Prometheus/Grafana metrics, audit logging, and high-availability features at custom pricing based on scale and requirements.
Quick Verdict: Best for organizations managing multiple isolated networks, large-scale edge device deployments requiring native WireGuard config compatibility, or B2B scenarios demanding strict customer segmentation. Ideal for IoT operators prioritizing router integration and teams needing network-level isolation without ACL complexity. Not suitable for teams seeking plug-and-play simplicity or those managing single-network deployments where multi-network overhead provides no benefit.
4. Nebula
Nebula is an open-source overlay networking tool created by Slack, released under the MIT License in 2019. Unlike commercial platforms, Nebula has no vendor, no pricing tiers, no feature gates, and consequently, no official support channels or service level agreements. Organizations gain unlimited deployment rights and total operational control but assume full responsibility for implementation, certificate management, and troubleshooting.
Why choose Nebula over Tailscale?
Nebula eliminates vendor dependency not through self-hosted coordination servers but by removing the vendor entirely. The project has no company extracting value, no roadmap prioritizing enterprise features over community needs, and no risk of pricing changes or acquisition. This architectural decision extends to infrastructure control, where Tailscale's coordination server manages identity and key exchange; Nebula uses a self-contained certificate authority model that operates independently without any external coordination dependency.
This independence creates distinct privacy advantages through ownership. Nebula's lighthouse nodes function as discovery coordinators by default; you control who sees your network topology. When peer-to-peer connections fail due to a restrictive NAT, lighthouses can optionally relay traffic, but critically, these relays run on infrastructure you operate.
Nebula's technical distinctions from Tailscale's WireGuard foundation:
- Certificate-Based PKI: Uses custom certificates asserting IP addresses, hostnames, and group memberships, eliminating coordination server dependency for identity management. Organizations control the certificate authority entirely, issuing credentials through the CLI tool without routing identity decisions through external infrastructure.
- Lighthouse Discovery Architecture: Employs lightweight discovery nodes with public IP addresses to coordinate peer-to-peer connections. Lighthouses function as discovery-only by default, though they can optionally relay encrypted traffic when direct connections fail, with the critical distinction that you operate this infrastructure rather than depending on vendor-controlled relays.
- Noise Protocol Framework: Implements the Noise_IX pattern with identity exchange on connection, differing from WireGuard's Noise_IK pre-shared model. Defaults to AES-256-GCM for performance while supporting ChaCha20-Poly1305 fallback, with identity sourced from signed certificates instead of coordination server state.
- Group-Based Firewall: Defines traffic filtering using certificate-embedded groups rather than coordination-server ACLs, enabling policy-as-code where access rules follow cryptographic identity instead of centrally managed configuration.
Remember, Nebula’s vendor-independence demands significant operational maturity. Manual certificate rotation requires coordinated trust bundle updates across all nodes; a multi-step procedure carrying production risk. All configuration occurs through YAML files without web interfaces, and certificate authority operations require command-line expertise. Community-only support means production issues rely on GitHub discussions rather than vendor SLAs.
Is Nebula free for commercial use?
Yes, Nebula operates under the permissive MIT License with no usage restrictions, deployment limits, or commercial licensing fees. Organizations can operate unlimited nodes in production without costs. However, "free" means freedom from licensing expenses, not freedom from operational burden. Teams must handle certificate infrastructure, troubleshooting, and security patching through internal expertise or community resources.
Organizations requiring commercial support can evaluate Defined Networking, a separate managed service founded by Nebula's creators that provides web UI and automated certificate management. This reintroduces vendor dependency that Nebula's architecture intentionally avoids, though it may suit teams wanting Nebula's approach without operational complexity.
Quick Verdict: Best for technically sophisticated teams comfortable with command-line tools, manual certificate management, and community-supported software. Ideal for organizations prioritizing vendor independence, metadata sovereignty, and total infrastructure control, and willing to invest engineering time in operational mastery. Not suitable for SMBs expecting commercial support, SLAs, or graphical administration interfaces, or teams lacking expertise to operate certificate infrastructure independently.
5. Innernet
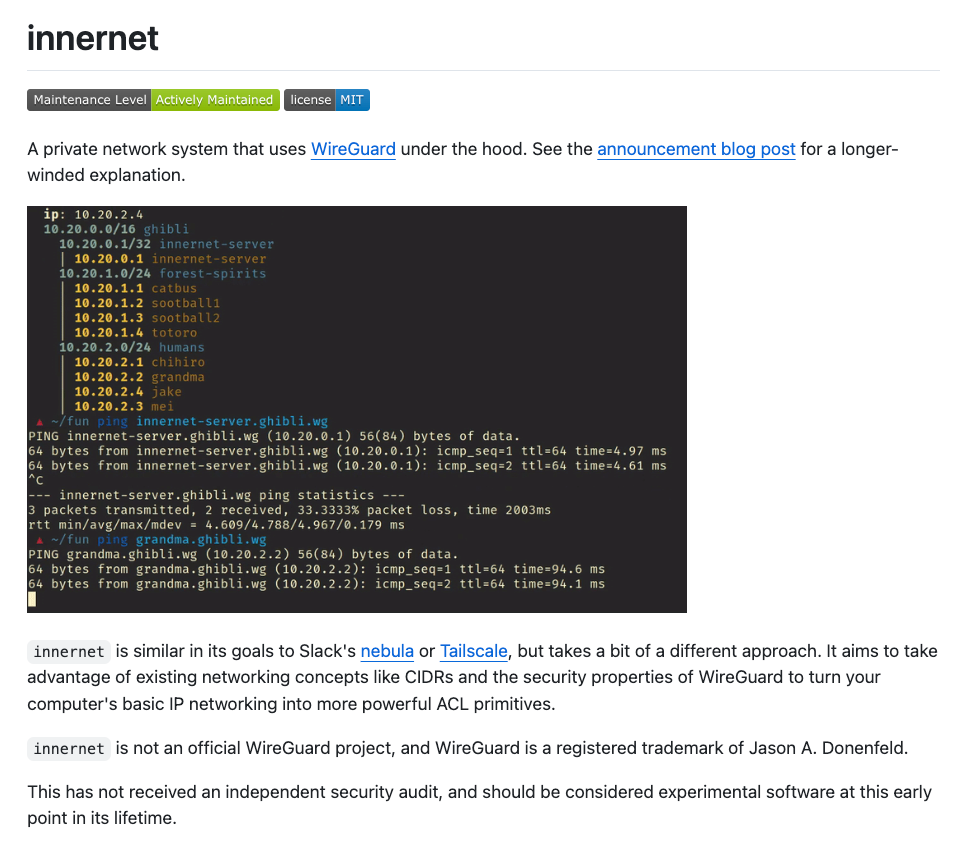
Innernet is an open-source private network system created by tonari, a Tokyo-based telepresence company, and released under the MIT License in 2021. Unlike platforms treating IP addressing as an implementation detail, Innernet organizes networks around hierarchical CIDR blocks, making subnet boundaries and IP ranges the fundamental organizational primitives for managing WireGuard mesh connectivity.
Why choose Innernet over Tailscale?
Innernet replaces Tailscale's flat network model with a hierarchical CIDR architecture where IP addresses define security boundaries. Tailscale assigns every node into a single flat /10 address space (100.x.y.z) where IP addresses are random assignments and security rules decouple from network topology through ACL tags. Innernet organizes networks as nested CIDR trees (e.g., carve a /16 for engineering, subdivide into /24s for teams, allocate /28s for infrastructure) where your IP address placement determines your security group membership and access permissions.
This CIDR-first philosophy proves intuitive for network administrators who think in subnet boundaries and IP ranges, providing familiar mental models from traditional networking. Organizations can express infrastructure segmentation through address allocation: development at 10.42.10.0/24, staging at 10.42.20.0/24, production at 10.42.30.0/24.
Innernet's distinguishing technical features include:
- Hierarchical CIDR Organization: Structures networks as nested IP ranges where subnet placement determines access permissions. Administrators allocate address blocks to define security boundaries rather than applying ACLs atop a flat topology.
- Kernel WireGuard Implementation: Manages native Linux kernel WireGuard interfaces by default rather than userspace implementations, though this limits cross-platform support compared to Go-based approaches.
- Invitation-Based Onboarding: Uses pre-generated invitation files for peer enrollment via , differing from SSO-driven authentication models that integrate with identity providers.
- Self-Hosted Coordination Only: Requires operating your own innernet-server for peer discovery and configuration distribution; no managed SaaS option exists.
Innernet's development pace reflects its origins as an internal tool open-sourced for community benefit. The project maintains ~60 contributors with approximately two releases annually, indicating active but modest maintenance rather than rapid feature development. The lack of dedicated relay infrastructure means peers behind symmetric NAT may struggle to establish connections without manual coordination. Moreover, all administration occurs through CLI tools without web interfaces.
Is Innernet free for commercial use?
Yes, Innernet operates under the MIT License with no restrictions on commercial deployment or usage scale. Organizations can operate Innernet networks in production without licensing costs. The project's maintenance model reflects small-team open source rather than commercially backed development with guaranteed response timelines or feature roadmaps.
Quick Verdict: Best for network administrators who think in CIDR blocks and want WireGuard mesh networking, mirroring traditional subnet architecture. Ideal for hobbyist deployments, homelab enthusiasts, and organizations comfortable with community-paced development and willing to maintain infrastructure independently. Not suitable for businesses requiring vendor support, guaranteed maintenance timelines, or teams needing managed services and commercial SLAs.
Which open source alternative should you choose?
NetBird delivers production-ready infrastructure with commercial backing, visual management tools, and active development. Organizations requiring vendor support, SSO integration, and feature velocity comparable to Tailscale will find NetBird the only genuine commercial alternative here.
Headscale and Netmaker offer middle-ground solutions with active development but less polish. Headscale provides the safest Tailscale migration path through official client compatibility, while Netmaker's multi-network architecture addresses segmentation requirements that the others handle through ACLs alone.
Nebula and Innernet represent pure community infrastructure; genuinely free and vendor-independent, but requiring teams comfortable operating certificate infrastructure and troubleshooting without vendor support. Nebula benefits from Slack's production validation and larger community; Innernet offers an elegant CIDR-centric design with modest ongoing development.
The strategic question: do you need commercial backing and ongoing feature development, or do you have the expertise and risk tolerance for community-maintained infrastructure?
Technical Specifications Comparison
| Platform | Open Source | Self-Hosting | Cloud Option | Key Differentiator |
|---|---|---|---|---|
| NetBird | BSD 3-Clause (client) + AGPLv3 (server) | Yes, core features (cloud-exclusive: IdP sync, SIEM streaming) | Yes (SaaS) | Control Center topology visualization + identity-aware SSH |
| Headscale | BSD 3-Clause | Yes, full features | No | Tailscale client compatibility without proprietary coordination |
| Netmaker | Apache 2.0 + SSPL | Yes, core features (paid: metrics, failover, user mgmt) | Yes (SaaS) | Multi-network segmentation + native WireGuard config support |
| Nebula | MIT | Yes, full features | Via Defined Networking | Certificate-based PKI + metadata sovereignty + community ownership |
| Innernet | MIT | Yes, full features | No | Hierarchical CIDR organization with subnet-based security |
Strategic Fit Analysis
| Platform | Ideal Use Case | Notable Limits |
|---|---|---|
| NetBird | Regulated industries, enterprises requiring vendor support, teams needing visual management and SSO integration | Per-user pricing scales with team size; self-hosted lacks some cloud features |
| Headscale | Self-hosters wanting Tailscale client UX with private coordination, small technical teams, homelab enthusiasts | Single-tailnet architecture limits multi-tenant scenarios; CLI-only administration |
| Netmaker | MSPs managing multiple customer networks, IoT deployments requiring router integration, multi-tenant scenarios | Usage-based pricing complexity; multi-network architecture adds operational overhead |
| Nebula | Organizations prioritizing metadata sovereignty and vendor independence with network engineering expertise | Manual certificate management; YAML-only configuration; community-only support |
| Innernet | Teams thinking in IP ranges/subnets, organizations comfortable with community-paced development | Two releases annually; lacks relay infrastructure for complex NAT scenarios; CLI-only |
Key Takeaways:
- Best for production readiness: NetBird (commercial backing, Control Center visualization, active development)
- Best for policy-driven segmentation: NetBird (group-based access control with granular policies)
- Best for network-level multi-tenancy: Netmaker (dedicated network isolation with CIDR flexibility)
- Best for Tailscale compatibility: Headscale (official client support without proprietary coordination)
- Best for vendor independence: Nebula (pure community ownership, metadata sovereignty)
- Best for traditional network admins: Innernet (hierarchical CIDR model with familiar subnet semantics)
Choose based on what you're optimizing for: commercial support and feature velocity, compatibility and simplicity, architectural flexibility, vendor independence, or operational familiarity. All five platforms deliver secure mesh networking; the differentiation lies in organizational fit and operational philosophy.
