ZeroTier pioneered software-defined networking for distributed teams, but its reliance on a custom protocol and Layer 2 architecture creates friction for modern cloud-native workflows. Engineering teams encounter performance bottlenecks from user-space packet processing, struggle with manual configurations in Kubernetes environments, and face limitations in integrating with enterprise identity providers for access management.
This guide evaluates five leading ZeroTier alternatives, both free and paid, exploring their technical architectures, deployment models, and ideal use cases. We compare protocol performance, authentication mechanisms, and management capabilities to help you identify the solution that fits your infrastructure requirements.
1. NetBird
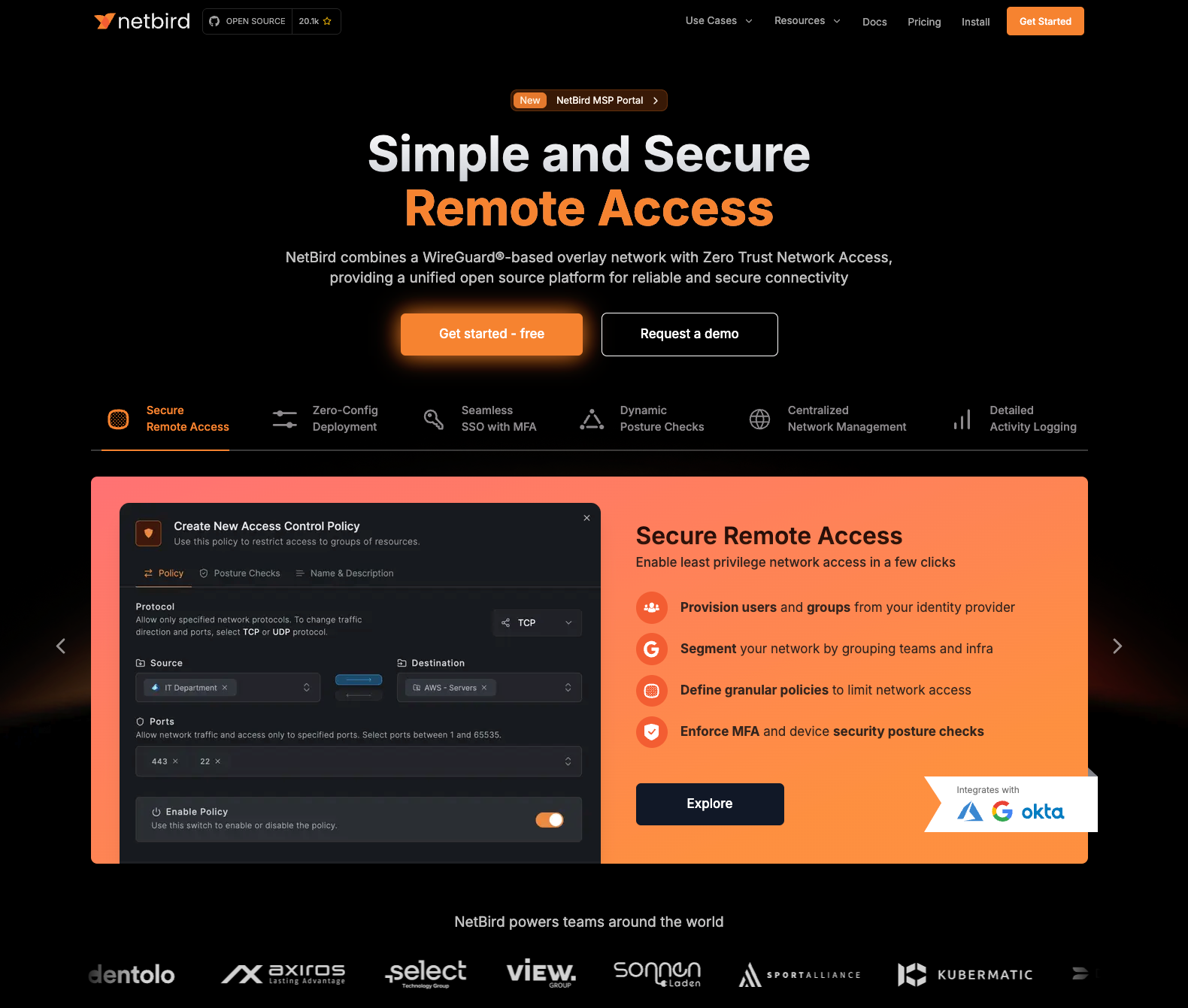
NetBird is an open-source Zero Trust networking platform combining WireGuard-based overlay networks with centralized access management. Devices connect directly over encrypted tunnels using advanced NAT traversal, with no centralized VPN gateway. Headquartered in Berlin, Germany, NetBird provides enterprises with a rapidly maturing alternative to legacy VPN solutions that enable DevOps and security teams to manage hybrid cloud infrastructure without complex firewall configurations or manual key distribution.
Why choose NetBird over ZeroTier?
NetBird uses kernel WireGuard instead of ZeroTier's custom userspace protocol, delivering 2-3× faster throughput by processing packets directly in the kernel. Moreover, ZeroTier gates critical features like SSO authentication and centralized web dashboard behind enterprise paywalls, while NetBird provides native SSO integration (Google, Microsoft, GitHub) with centralized UI for policy management; all available in the free tier. Regarding data sovereignty, NetBird's Berlin headquarters and self-hosting capabilities ensure GDPR compliance that most SaaS-only alternatives cannot match.
The key features that separate NetBird from ZeroTier are:
- Complete feature parity ensures self-hosted deployments include all enterprise capabilities (Control Center UI, SSO, access policies, DNS management) available in the SaaS version; ZeroTier's self-hosted controller strips these features, leaving teams with API-only management.
- Control Center provides an interactive topology map to instantly audit 'who can access what,' replacing ZeroTier’s spreadsheet-style lists with real-time visualization.
- Identity-Aware SSH eliminates manual key management by injecting native IdP authentication using OIDC/JWT tokens directly into OpenSSH sessions, instantly revoking access when a user leaves the organization.
- NetBird Networks simplifies site-to-site connectivity with native High-Availability routing; unlike ZeroTier, which requires complex configuration for redundant gateways, NetBird creates self-healing entry points to your VPCs and LANs automatically.
Is NetBird free for commercial use?
Yes, NetBird's free tier supports up to 5 users and 100 machines with full peer-to-peer connectivity, access control policies, network routing, and DNS management, suitable for small teams and individual projects.
Paid plans ($5-12/user/month) add priority support, SSO/MFA integration, Identity-Aware SSH, device posture checks with MDM/EDR integration (CrowdStrike, Intune, SentinelOne), and SIEM logging for compliance.
Quick Verdict: Best for engineering teams requiring kernel-level performance with centralized visibility through Control Center. Strong choice for EU organizations with GDPR mandates, though NetBird serves global deployments equally well. Ideal for teams wanting open-source flexibility with optional managed services, avoiding vendor lock-in while maintaining enterprise features like Identity-Aware SSH and native SSO integration.
2. Tailscale
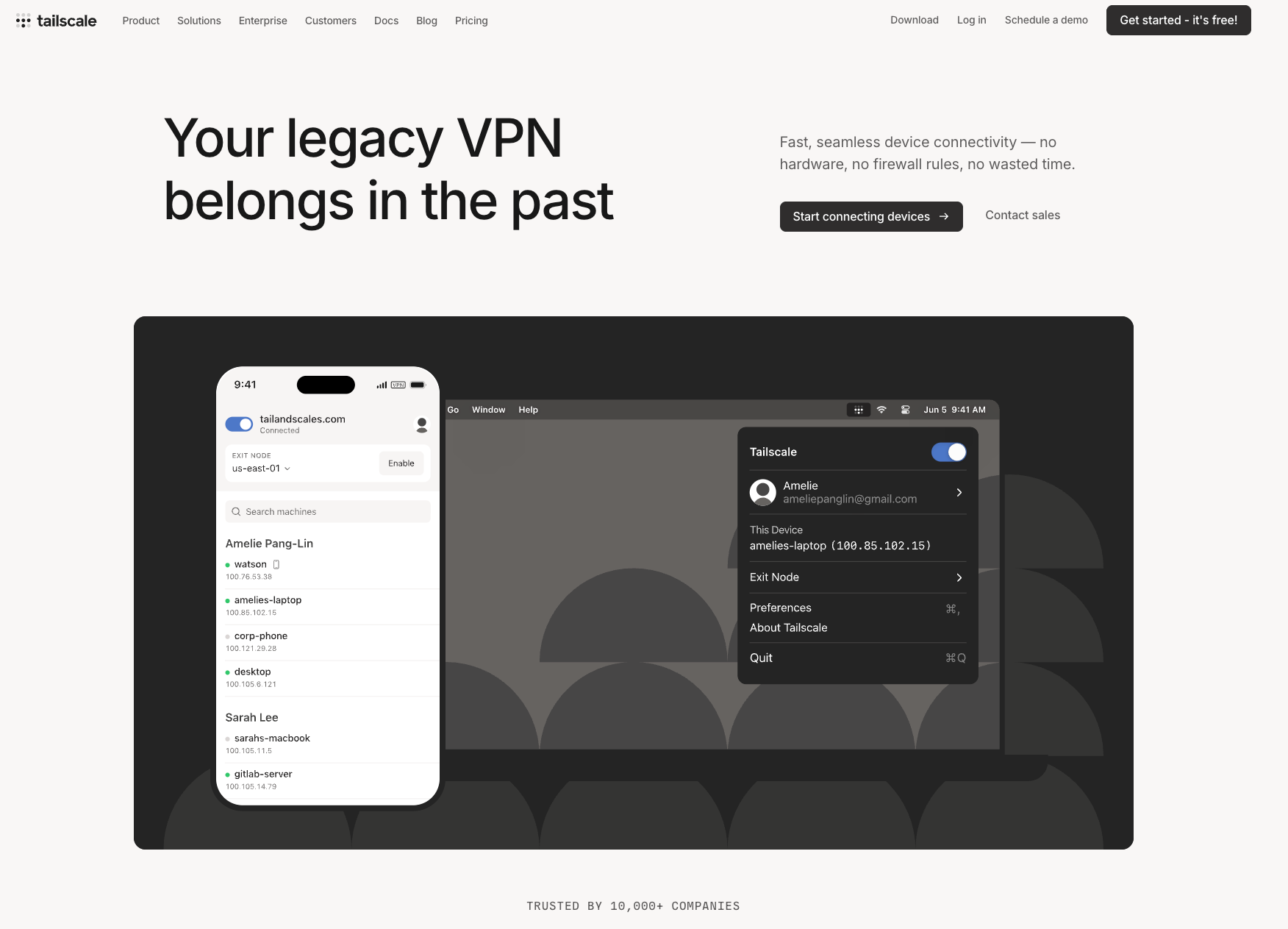
Like NetBird, Tailscale is a mesh VPN built on the WireGuard protocol that simplifies secure networking through automated NAT traversal and identity-based access controls. However, while Tailscale's client applications are open source, the platform operates as a SaaS solution with a proprietary coordination server managing device registration, key exchange, and network policies. Known for exceptional user experience and rapid deployment, Tailscale has become popular with developers, IT teams, and organizations seeking to eliminate traditional VPN complexity.
Why choose Tailscale over ZeroTier?
Tailscale delivers zero-configuration networking through complete automation of peer discovery, key exchange, and ACL distribution, therefore eliminating the manual network setup that traditional VPNs require. Unlike ZeroTier’s reliance on manual scripting for access control (Flow Rules), Tailscale utilizes JSON-based ACL policies with human-readable syntax. The platform's native SSO integration with major IdPs (Google, Microsoft, GitHub, Okta) means engineers connect using corporate credentials rather than managing separate authentication layers.
Teams prioritizing operational simplicity choose Tailscale for these core features.
- Coordination server automation handles key rotation, peer discovery, and policy distribution without self-hosted infrastructure, contrasting with ZeroTier's requirement to manage network controllers and manual ACL configuration
- MagicDNS automatically assigns human-readable names to every device (e.g., ), eliminating IP address management and enabling seamless service discovery across your network
- Tailscale SSH manages SSH authentication and authorization through your identity provider, replacing manual key distribution that both ZeroTier and traditional SSH workflows require; though session recording capabilities remain Enterprise-only
- DERP relay network provides globally distributed, professionally maintained relay infrastructure, ensuring reliable connectivity when direct peer-to-peer connections fail due to restrictive NAT configurations
However, Tailscale’s managed coordination server becomes a single point of trust, which can be a significant hurdle for organizations operating in heavily regulated industries or those with stringent security and compliance mandates.
Is Tailscale free for commercial use?
No, Tailscale's Personal plan is free for up to 3 users and 100 devices, but explicitly limited to personal, non-commercial use. Organizations using work email domains are automatically enrolled in a 14-day Enterprise trial.
The Starter plan ($6/user/month annually) supports commercial deployments with unlimited users, subnet routers, exit nodes, and MagicDNS. Premium ($18/user/month annually) adds Tailscale SSH, network flow logging, advanced posture management, and service-level ACL grants. Enterprise pricing includes SSH session recording, SCIM provisioning, Tailnet Lock, and dedicated support channels.
Quick Verdict: Best for teams prioritizing ease of use and minimal operational overhead above infrastructure ownership. Ideal for organizations comfortable with managed SaaS models that don't require self-hosting capabilities. The proprietary coordination server and commercial-only licensing make Tailscale less suitable for teams with strict data sovereignty mandates or those seeking fully open-source alternatives like NetBird or Headscale.
3. Twingate
Twingate is a cloud-native Zero Trust Network Access (ZTNA) platform that replaces traditional VPNs with software-defined perimeters around individual resources. Unlike mesh VPN architectures that create peer-to-peer networks, Twingate employs a Connector-based model where lightweight proxy agents deployed within private networks broker access to specific applications and services. The platform enforces resource-level access controls rather than network-level permissions, making it particularly attractive to regulated industries requiring granular audit trails and compliance documentation.
Why choose Twingate over ZeroTier?
Twingate enforces application-level access isolation: policies grant access only to specific ports on specific resources, not entire network subnets. While ZeroTier's Managed Routes expose entire subnets via Layer 3 routing, Twingate's software-defined perimeters ensure that even if a connector is compromised, unauthorized services remain invisible to authenticated users. This architectural distinction proves critical for compliance-driven organizations: Twingate's identity-indexed logging captures which users accessed which specific resources at precisely what times, satisfying audit requirements for HIPAA, SOC 2, and financial services regulations.
For regulated enterprise environments, the platform offers specific advantages:
- Application-level isolation grants access only to specific application ports (e.g., tcp/443), ensuring the underlying server and broader network remain invisible. This approach contrasts with ZeroTier's subnet-level exposure
- Resource-level audit logging tracks every access attempt with forensic detail (user, device, resource, timestamp, duration), streaming to SIEM platforms for compliance reporting; network-layer approaches cannot provide this granularity
- Identity-native authentication integrates directly with enterprise IdPs through SCIM for automated provisioning, with universal MFA extending to SSH, RDP, and legacy protocols
- QUIC-based transport provides faster connection establishment than traditional protocols, supports connection roaming across network changes (Wi-Fi to LTE), and enables multiplexed application streams for reduced latency
Like Tailscale, Twingate operates as a cloud service; organizations cannot self-host the control plane. For teams requiring complete infrastructure ownership or strict data sovereignty mandates, this SaaS-only model creates dependency on Twingate's infrastructure that self-hostable alternatives like NetBird, Headscale, or Nebula avoid.
Is Twingate free for commercial use?
No, Twingate's Starter plan is free but limited to personal use and testing with up to 5 users and 10 remote networks, including basic split tunneling and conditional access controls.
The Teams plan ($5/user/month annually) supports commercial deployments up to 100 users and 20 networks, adding SSO via Google Workspace, SaaS application gating, device posture checks, and MFA for SSH. Business ($10/user/month annually) supports up to 500 users with advanced SSO, comprehensive MDM/EDR integrations, service accounts, and detailed audit logging with SIEM/S3 sync capabilities. Enterprise offers custom pricing with unlimited users, DNS filtering, geoblocking, DLP controls, and dedicated support.
Quick Verdict: Best for security-conscious organizations in regulated industries (healthcare, finance, legal) requiring application-level access controls and comprehensive audit trails for compliance. The cloud-only deployment model suits teams comfortable with managed services but eliminates options for organizations requiring self-hosted control planes or complete infrastructure ownership.
4. Nebula
Nebula is an entirely free, open-source overlay networking tool developed by Slack to connect tens of thousands of production hosts across global infrastructure. Built on the Noise Protocol Framework rather than WireGuard, Nebula uses a PKI-based certificate model where administrators manually generate and distribute cryptographic credentials for each host. The open-source project operates as self-hosted infrastructure with no subscription fees or centralized coordination servers, though the creators have founded Defined Networking to offer a managed commercial version for organizations preferring vendor support.
Why choose Nebula over ZeroTier?
Nebula eliminates all external infrastructure dependencies through offline certificate-based authentication. Once certificates are distributed, hosts authenticate peers cryptographically without internet connectivity to coordination servers or identity providers. While ZeroTier requires connection to root servers for peer discovery and network controllers for configuration, Nebula's lighthouse nodes operate entirely within your infrastructure. For air-gapped environments, research institutions, or organizations with strict data sovereignty mandates, this self-contained model proves invaluable.
Infrastructure purists choose Nebula for the following architectural benefits:
- Certificate-based trust model eliminates dependency on external services. Administrators generate a certificate authority offline, then sign host certificates containing IP addresses and group memberships; hosts authenticate peers cryptographically without coordination servers
- Complete air-gap capability enables networks to function entirely offline indefinitely; in contrast, ZeroTier requires internet connectivity for peer discovery through root servers, making complete air-gapping significantly more complex
- MIT license provides true open-source freedom without commercial restrictions; ZeroTier's Business Source License restricts certain commercial uses and includes proprietary components
- Battle-tested at scale powers Slack's production overlay connecting over 50,000 hosts across multiple cloud providers, demonstrating real-world scalability and reliability for large deployments
However, this architectural simplicity comes with operational overhead: administrators manually run commands to generate credentials, distribute configuration files to each host via tools like Ansible or Terraform, maintain lighthouse nodes with static IPs for peer discovery, and handle certificate rotation before the default one-year expiration.
Organizations comfortable with infrastructure-as-code workflows and command-line tools will find Nebula's approach transparent and controllable; teams expecting GUI dashboards and automated onboarding can consider Defined Networking's managed offering.
Is Nebula free for commercial use?
Yes, open-source Nebula is completely free for any use, including commercial deployments. Released under the MIT license, organizations can use, modify, and redistribute Nebula without licensing fees, revenue sharing, or usage restrictions. There are no tiered plans, device limits, or premium features; every capability is available in the single open-source release.
Operational costs are limited to infrastructure: lightweight cloud instances for lighthouse nodes (typically $5-10/month for small networks), engineering time for certificate management and configuration distribution, and internal support for troubleshooting.
For organizations that prefer managed services, Defined Networking (founded by Nebula's creators) offers a commercial version with web UI, automated certificate management, and vendor support.
Quick Verdict: Best for technical teams prioritizing complete infrastructure ownership, organizations with air-gapped requirements, or budget-conscious deployments where engineering time substitutes for commercial support costs. Not suitable for businesses requiring immediate vendor SLAs or non-technical user onboarding without considering the managed alternative.
5. Headscale
Headscale is an open-source, self-hosted implementation of the Tailscale coordination server, enabling organizations to use official Tailscale clients without dependency on Tailscale's commercial SaaS infrastructure. Unlike Nebula, which requires custom clients, Headscale maintains compatibility with Tailscale's native applications across all platforms. Users install standard Tailscale clients but point them to a privately hosted Headscale server. This approach appeals to homelabbers, privacy-focused organizations, and technical teams who value Tailscale's user experience but require complete infrastructure ownership.
Why choose Headscale over ZeroTier?
Headscale delivers Tailscale's polished user experience through self-hosted infrastructure. Users install familiar Tailscale applications providing MagicDNS, exit nodes, and subnet routers without learning new clients. In contrast to ZeroTier, which uses custom clients across all platforms, Headscale uses Tailscale's battle-tested applications for Windows, macOS, iOS, Android, and Linux. The authentication model offers a middle ground between commercial platforms and offline-only solutions: Headscale supports OIDC integration with providers like Authentik or Keycloak for web-based device registration, though OIDC groups cannot yet be used within ACL rules, requiring manual user-to-group mapping.
Key technical differentiators for self-hosting enthusiasts include:
- Official Tailscale client compatibility works with unmodified Tailscale applications across all platforms. Users enjoy the same polished GUI, mobile apps, and OS integrations while backend coordination runs on private infrastructure
- Embedded DERP relay server provides built-in relay infrastructure for NAT traversal fallback, eliminating dependency on Tailscale's relay network while maintaining connection reliability when direct peer-to-peer paths fail
- Subnet routers and exit nodes offer full support for advertising subnet routes with automatic failover plus exit node capabilities for routing internet traffic; matching Tailscale's core routing features
- BSD 3-Clause license provides true open-source freedom for self-hosting Tailscale's client experience; however, compatibility depends on Tailscale maintaining protocol stability, creating potential future risks
Take into account that Headscale operates with significant limitations, including single-tailnet deployments (no multi-tenant capabilities), no official web UI for management (CLI and API only), OIDC groups cannot be used in ACL rules, and Tailscale SSH lacks session recording. Organizations receive no vendor support or compatibility guarantees; the community-driven project depends on volunteer maintainers and Tailscale's goodwill in maintaining protocol compatibility.
Is Headscale free for commercial use?
Yes, Headscale is completely free for any use, including commercial deployments. Released under the BSD 3-Clause license, organizations can deploy, modify, and operate Headscale indefinitely without licensing fees or usage restrictions.
Operational costs mirror Nebula's model: infrastructure for hosting the coordination server (modest resource requirements similar to running a small web application), engineering time for ACL management and troubleshooting, and internal support for users. The advantage over Nebula lies in client simplicity. Users install Tailscale client applications rather than learning new tools, but the trade-off is maintaining the coordination server and staying current with Headscale releases to preserve Tailscale client compatibility.
Quick Verdict: Best for technical enthusiasts, homelabbers, and small organizations looking for Tailscale's user experience without commercial dependency. Ideal for those comfortable with command-line administration and community support channels. Not suitable for organizations requiring vendor SLAs, multi-tenant capabilities, or GUI-based management.
Which ZeroTier alternative should you choose?
The right choice depends on your operational model: do you want a managed service, a self-hosted platform, or a pure peer-to-peer protocol?
NetBird occupies the middle ground, offering the ease of a managed SaaS with the flexibility of a fully open-source self-hosted option. It stands out for teams that need visual topology management (Control Center) and identity-backed SSH controls without being locked into a proprietary platform. Its German headquarters also offers a distinct data sovereignty advantage for EU-based organizations compared to US-centric providers.
Tailscale remains the gold standard for user experience and ecosystem maturity. If your priority is "it just works" and you are comfortable with a closed-source coordination server, it is the path of least resistance. Twingate is the specialist choice for compliance-heavy industries, trading peer-to-peer mesh benefits for granular, resource-level access logs that satisfy strict auditors.
For infrastructure purists, Nebula delivers battle-tested performance (proven at Slack) with zero external dependencies, while Headscale allows you to use Tailscale’s polished clients while retaining backend ownership. Both require significant DevOps maturity and lack official vendor support.
The tables below summarize technical capabilities and strategic positioning to guide your evaluation:
Table A: Technical Specifications
| Solution | Open Source | Self-Hosted | Cloud SaaS | Key Differentiator |
|---|---|---|---|---|
| NetBird | ✓ | ✓ | ✓ | Visual topology, Self-hosted SSO & SSH, EU Compliance |
| Tailscale | Partial (Clients) | ✗ | ✓ | Zero-config UX, MagicDNS, massive integration ecosystem |
| Twingate | ✗ | ✗ | ✓ | Forensic Logging, Resource-level hiding (SDP) |
| Nebula | ✓ | ✓ | ✗* | Certificate-based trust, Air-gap capable, MIT License |
| Headscale | ✓ | ✓ | ✗ | Tailscale Client compatibility with self-hosted backend |
*Managed SaaS available via third-party (Defined Networking), but not native to the project.
Table B: Strategic Fit
| Solution | Ideal Use Case | Notable Trade-offs |
|---|---|---|
| NetBird | Teams wanting a "Tailscale-like" experience but with Data Sovereignty and Self-Hosting | Smaller ecosystem than Tailscale (rapid maturation) |
| Tailscale | Developers and IT teams prioritizing maximum convenience and integration | Proprietary control plane; expensive for compliance features |
| Twingate | Regulated Enterprises (HIPAA/SOC2) needing audit trails over mesh connectivity | SaaS-only (No self-hosting); higher cost per user |
| Nebula | DevOps & Platform Teams needing scalable, air-gapped infrastructure | High operational overhead (Manual config); No native GUI |
| Headscale | Homelabbers & Privacy Techs who love Tailscale apps but hate vendor lock-in | Single-tenant only; relies on community support |
Key Takeaways
- Choose Tailscale if you want the polished "Apple-like" experience and don't mind the vendor lock-in.
- Choose NetBird if you want the modern feature set (SSO, SSH, Dashboard) but require open-source ownership or GDPR compliance.
- Choose Twingate if your primary goal is hiding internal resources for compliance audits.
- Choose Nebula/Headscale if you have the engineering time to trade for absolute control and zero licensing costs.
