NetBird's access control policies had a significant limitation: when you configured ALL or ICMP protocol access between peers, traffic flowed in both directions by default. Our previous method for handling reply traffic opened the reply path based on the reversed connection details, which worked for specific TCP or UDP ports but created limitations and was too rigid for broader policies like ALL where reply ports couldn't be predicted. This gap significantly limited true Zero Trust micro-segmentation.
NetBird's new unidirectional access control policies required different approaches depending on the platform. On Linux, NetBird leverages native firewall capabilities with established rules like that automatically handle reply traffic through the kernel's connection tracking. For non-Linux platforms where NetBird doesn't integrate with native firewalls, we built our own stateful firewall in userspace with a connection tracker that dynamically creates temporary rules for reply traffic on demand. For TCP, we track the full state machine. For UDP and ICMP, we track sessions using timeouts. This essentially recreates what Linux firewalls accomplish with "related, established" connection states, but entirely in userspace.
The frontend changes were more straightforward: removing the restrictions in both the API and UI that previously forced ALL, ICMP, and all-ports TCP/UDP policies to be bidirectional. The new interface provides intuitive direction indicators and smart warnings when you select network resources as the destination, eliminating guesswork about policy direction.
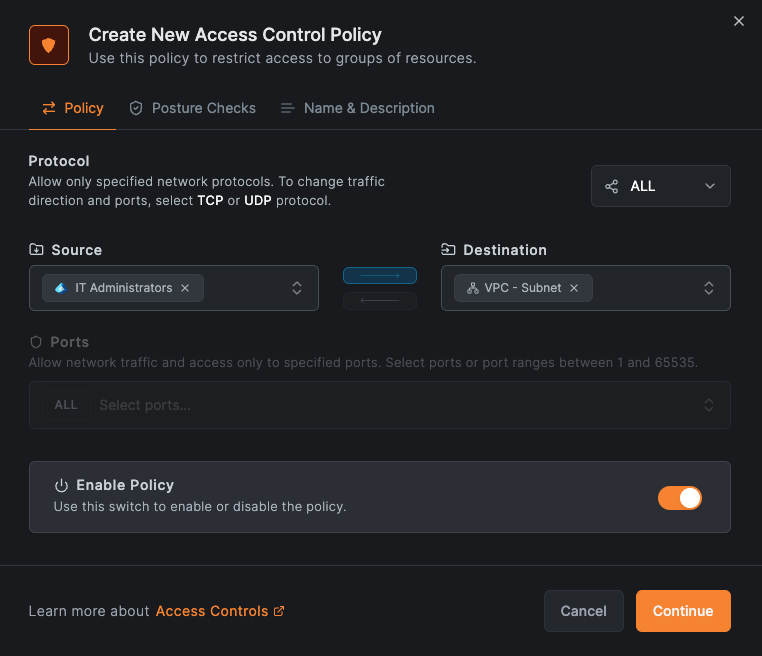
The security impact is immediate and powerful. Unidirectional policies enforce a fundamental principle: backend resources shouldn't initiate outbound connections. Your application servers maintain full access to databases and file servers, but those backend systems can't reach back out to applications or other systems. If a database gets compromised, it stays contained instead of becoming a launching point for network-wide attacks.
Available in NetBird version v0.36.6, this capability delivers the enterprise-grade directional access control that makes Zero Trust implementations actually work as intended.
